Make Your Computer go Green October 2, 2008
Posted by Abdurahman in technology.Tags: electronics, green, green computer, low energy, power management, power saver
2 comments
After all, the machine that can provide you with information on how to lead an ecologically sound life can also be contributing to the environmental problem you are trying to solve. (more…)
Selamat Hari Raya Idul Fitri October 1, 2008
Posted by Abdurahman in Uncategorized.3 comments
..Disaat waktu berdetak..
..Kesalahan ikut meningkat..
..Disaat hari yang fitri..
..Maafkan khilaf yang terjadi..
..Hingga semua dosa yang ada..
..Semuanya terbang ke udara..
..Jadikan jiwa kita laksana..
..Bayi yang lahir ke dunia..
..Since we are a human..
..Many error we made..
..Forgiveness is the only way to enter the god’s heaven..
..Lets together we enter thats heaven..
..Taqoballahu minna wa minkum..
..Shiyamana Wa Shiyamakum..
..Minal Adzin Wal Faidzin..
September 29, 2008
Posted by Abdurahman in Quotes.Tags: dell, michael, quote
add a comment
If you want to sustain excellence over a long time, you’d better come up with a system that works well. Anyone can sprint for a little while, but you can’t sprint for forty years.
Michael Dell;From the books Direct From Dell(p.xxvi)
Looking inside CERN:LHC servers September 23, 2008
Posted by Abdurahman in technology.Tags: CERN, LHC, SERVERS
1 comment so far
I found interesting pictures in Royal Pingdom website.
It says that CERN’s Large Hadron Collider (LHC) will be producing roughly 15 petabytes of data each year (15,000,000,000,000,000 bytes). In other words, the LHC is not only huge in physical size (filling a 17-mile long underground path), but it will produce enormous amounts of data for researchers to bite into.
Here are some of the pictures(Warning: High-res picture inside)
Apple menarik kembali adaptor iPhone 3G September 21, 2008
Posted by Abdurahman in news.Tags: iPhone recalled
1 comment so far
Apple diberitakan telah menarik kembali adapter untuk iPhone 3G pada hari Jum’at, 19 September kemarin lusa.
Seperti dikutip dari Cnet news, hal ini disebabkan banyaknya laporan bahwa adapter tersebut cacat produksi dan dapat mengakibatkan arus pendek yang dapat menyebabkan kerusakan pada iPhone hingga kebakaran.
Namun Apple sendiri menjamin bahwa penarikan tersebut akan diiringi dengan penggantian adapter baru yang telah disempurnakan tanpa biaya sama sekali.
Hingga berita ini dilansir dari situs resmi Apple, belum ada laporan mengenai adanya korban jiwa karena cacat produksi ini.
Apple mengeluarkan produk inovatifnya iPhone 3G beberapa saat yang lalu sebagai tanda bahwa Apple Corp. tertarik untuk bersaing di pasar mobile phone. Apple mengeluarkan teknologi yang dimilikinya antara lain layar multi-sentuh, kemampuan memainkan musik mp3, hingga kamera built-in resolusi tinggi 2.0 MP di produk mobilenya ini. Meskipun ini produk pertama dari Apple, sambutan pasar sangat luar biasa sekali.
Meskipun cacat produksi, para pengguna yang baru saja membeli iPhone setelah hari Jum’at kemarin. iPhone dengan tanda lingkaran hijau kecil di atas kemasannya menggunakan adapter yang sudah disempurnakan.
Sayangnya produk ini belum ada di Indonesia :p
Information Security, What to protect ? (Part-2) September 17, 2008
Posted by Abdurahman in technology.Tags: key concept, security
1 comment so far
After three key concept in my previous post. Now I will describe what the others concept to securing information.
4. Authenticity
in computing areas, you have to make sure that people who have access to certain information are eligible to access it. Username and Password are the basic things from this concept.
5. Non-repudiation
This is mean, you can’t denied any transaction written on the computer. For example, if you has bought something from popular E-commerce site, in the future you denied that you ever bought something from there. and this problem goes into the law, the court will ask for the log-file of your transaction as a proof. Log files can be used as a proof <– this is mean of non-repudiation. Nowadays, digital signatures are commonly used as part of non-repudiation.
6. Logical Security
Wider area to securing information. Like username and password before you login to your computer.
8. Physical Security
Commonly use of biometrics for authentication (e.g. Fingerprint reading, Voice Recognition etc..)
Turning Research into Real World Business: A critic to Indonesian Government September 17, 2008
Posted by Abdurahman in Opinion.Tags: critics, Opinion, research, supertoy
4 comments
This is the second time Indonesian government have a big failure in research area. Of course research always possible to fail, but this fail is too big since it’s become national issue. Its an ironic the guy who cause the failure is the same guy. We all knows that only donkeys can fall in the hole for twice. What I mean is about Supertoy Rice.
It’s a normal thing if Indonesia wants to solve food problems. You can produce more rice within the same area. But research has a method to follow or your research will be either over budget or totally failed. I’m just a student who trying to give my opinions so this problems will not occur in the future.
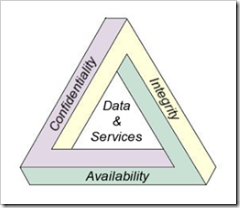
Information Security, what to protect? September 16, 2008
Posted by Abdurahman in technology.Tags: information security, key concept, security concept
1 comment so far
For some institution(business, government etc.) they need to secure their information from outside threat. This threat could be from anywhere. It can be from either from outside or inside. They are not trying to protect the hardware. When the hardware is broken or stolen, you still can find its replacement on the market; They also not trying to protect their software, its always can be reinstalled again, even it takes time. It is the information they were trying to protect. Information of their customer, civilian records, financial records. Most of it are stored within popular office format such as Word, Excel, Access or even in database like MySql, PostgreSQL, Oracle or any popular database vendors.
Here I’m trying to describe what is the key concept how to secure this kind of information.
1. Confidentiality
Confidentiality means that you are trying to protect some information from unauthorized access, such as hackers, crackers, and any people/subject that don’t have rights to access sort of information you have.
2. Integrity
Even it’s protected, you have to ensure that your information is not altered by mistake or accidents. So the information need to be authorized first before you can make some changes on it.
3. Availability
It’s useless if you are protected something but that information is not available to you when you need it.
Those key concept are well known as CIA concept. I will adding more key concept in my next post.
Next Generation LCD September 15, 2008
Posted by Abdurahman in technology.Tags: lcd, research, techo, transparent, transparent lcd
4 comments
Have you ever imagine what is the next LCD monitor look like?
Well, I admit that I have no idea about that. Until today, I just got a forwarded e-mail from my colleague in APIIT give me a ‘sneak-peek’ about the next generation LCD.
Are you interested to know further?
Quote of the day September 4, 2008
Posted by Abdurahman in Quotes.add a comment

“The only thing that certain in this world, is the uncertainty itself..”
Albert Einstein