Symbian will switch to Open Source October 26, 2008
Posted by Abdurahman in news, technology.Tags: nokia, open source, switch, Symbian
2 comments
 According to ZDNet online, Symbian is switching to Open Source after being taken to Nokia. Open Source now will developing it’s own business model.
According to ZDNet online, Symbian is switching to Open Source after being taken to Nokia. Open Source now will developing it’s own business model.
They will start full open source at 2010.
Microsoft release unusual patch for Windows October 25, 2008
Posted by Abdurahman in news, technology.Tags: microsoft, patch, software, update, windows update
add a comment
 Microsoft will release an emergency security patch for Windows tonight. This is unusual, as Microsoft typically releases security patches only once per month on what has become known as “Patch Tuesday.” The rushed release may indicate that the security hole puts users at greater than usual risk.
Microsoft will release an emergency security patch for Windows tonight. This is unusual, as Microsoft typically releases security patches only once per month on what has become known as “Patch Tuesday.” The rushed release may indicate that the security hole puts users at greater than usual risk.
A little more information can be found here and here. If you are a Windows user and you do not use Automatic Updates (which you probably should), or if you are a Windows sysadmin, you may want to go out of your way tomorrow morning to download and install the new patch. Home and small office users can do so via Windows Update, which can be found in the Start menu and/or in the Tools menu of Internet Explorer.
Apple wants to built University October 24, 2008
Posted by Abdurahman in news, Opinion, technology.Tags: apple, dean, Silicon alley insider, university, yale
add a comment
 Dan Former, Writing in Silicon Alley Insider mentioning that Apple is willing to build their own university. They hiring the dean of Yale’s business school to start it.
Dan Former, Writing in Silicon Alley Insider mentioning that Apple is willing to build their own university. They hiring the dean of Yale’s business school to start it.
In My Humble Opinion, there will be design faculty, engineering and other technology faculty related to apple’s business. I just hope that the fees there is not as expensive as harvard.
The biggest thing from Apple is they can turn innovation to make money, will they teach that thing in the class?
Interested to Join? 🙂![]() apple university
apple university
Office-14, It’s all on the cloud. October 21, 2008
Posted by Abdurahman in news, technology.Tags: cloud computing, internet cloud, microsoft, office, office 14, PDC, professional developer conference, sneak-peek, steve ballmer, windows 7
2 comments
“We will rewrite Office to work in a browser”, as Steve Ballmer on Interview with Computer Weekly.
Microsoft is preparing for it’s Professional Developer Conference next week. Some attendees are likely to get a peek at a couple of Windows 7 features.
Tentang Cloud Computing October 6, 2008
Posted by Abdurahman in Opinion, technology.Tags: chrome, cloud computing, google, komputasi awan, microsoft, opini, teknologi
9 comments
Saya akan menuliskan posting berikut pada Bahasa Indonesia, karena nampaknya di Indonesia masih “awam” tentang konsep ini. Saya harapkan, tulisan saya akan sedikit mencerahkan pembaca, mengingat teknologi informasi saat ini akan berkembang ke arah sana.
Cloud Computing…Barang apa lagi itu??
Kalau diterjemahkan secara literal sih, maknanya komputasi awan, yang ada malah bikin bingung. Nah, penjelasan yang saya ambil dari berbagai sumber, maksudnya itu kegiatan komputasi yang dijalankan sebagaian besar di server. sedangkan klien hanya “menampilkan” hasilnya saja. Komputasi disini maknanya bukan hanya menghitung loh, bisa mengolah, menyimpan dan menghapus. (more…)
(more…)
Make Your Computer go Green October 2, 2008
Posted by Abdurahman in technology.Tags: electronics, green, green computer, low energy, power management, power saver
2 comments
After all, the machine that can provide you with information on how to lead an ecologically sound life can also be contributing to the environmental problem you are trying to solve. (more…)
Looking inside CERN:LHC servers September 23, 2008
Posted by Abdurahman in technology.Tags: CERN, LHC, SERVERS
1 comment so far
I found interesting pictures in Royal Pingdom website.
It says that CERN’s Large Hadron Collider (LHC) will be producing roughly 15 petabytes of data each year (15,000,000,000,000,000 bytes). In other words, the LHC is not only huge in physical size (filling a 17-mile long underground path), but it will produce enormous amounts of data for researchers to bite into.
Here are some of the pictures(Warning: High-res picture inside)
Information Security, What to protect ? (Part-2) September 17, 2008
Posted by Abdurahman in technology.Tags: key concept, security
1 comment so far
After three key concept in my previous post. Now I will describe what the others concept to securing information.
4. Authenticity
in computing areas, you have to make sure that people who have access to certain information are eligible to access it. Username and Password are the basic things from this concept.
5. Non-repudiation
This is mean, you can’t denied any transaction written on the computer. For example, if you has bought something from popular E-commerce site, in the future you denied that you ever bought something from there. and this problem goes into the law, the court will ask for the log-file of your transaction as a proof. Log files can be used as a proof <– this is mean of non-repudiation. Nowadays, digital signatures are commonly used as part of non-repudiation.
6. Logical Security
Wider area to securing information. Like username and password before you login to your computer.
8. Physical Security
Commonly use of biometrics for authentication (e.g. Fingerprint reading, Voice Recognition etc..)
Information Security, what to protect? September 16, 2008
Posted by Abdurahman in technology.Tags: information security, key concept, security concept
1 comment so far
For some institution(business, government etc.) they need to secure their information from outside threat. This threat could be from anywhere. It can be from either from outside or inside. They are not trying to protect the hardware. When the hardware is broken or stolen, you still can find its replacement on the market; They also not trying to protect their software, its always can be reinstalled again, even it takes time. It is the information they were trying to protect. Information of their customer, civilian records, financial records. Most of it are stored within popular office format such as Word, Excel, Access or even in database like MySql, PostgreSQL, Oracle or any popular database vendors.
Here I’m trying to describe what is the key concept how to secure this kind of information.
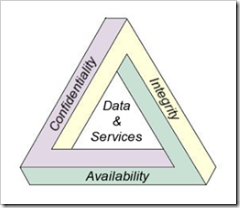
1. Confidentiality
Confidentiality means that you are trying to protect some information from unauthorized access, such as hackers, crackers, and any people/subject that don’t have rights to access sort of information you have.
2. Integrity
Even it’s protected, you have to ensure that your information is not altered by mistake or accidents. So the information need to be authorized first before you can make some changes on it.
3. Availability
It’s useless if you are protected something but that information is not available to you when you need it.
Those key concept are well known as CIA concept. I will adding more key concept in my next post.
Next Generation LCD September 15, 2008
Posted by Abdurahman in technology.Tags: lcd, research, techo, transparent, transparent lcd
4 comments
Have you ever imagine what is the next LCD monitor look like?
Well, I admit that I have no idea about that. Until today, I just got a forwarded e-mail from my colleague in APIIT give me a ‘sneak-peek’ about the next generation LCD.
Are you interested to know further?